Generating Encrypted Document Index Structure Using Tree Browser
DOI:
https://doi.org/10.51173/jt.v5i2.948Keywords:
B±Tree, Encryption, Information Retrieval, Inverted Index, TB-TreeAbstract
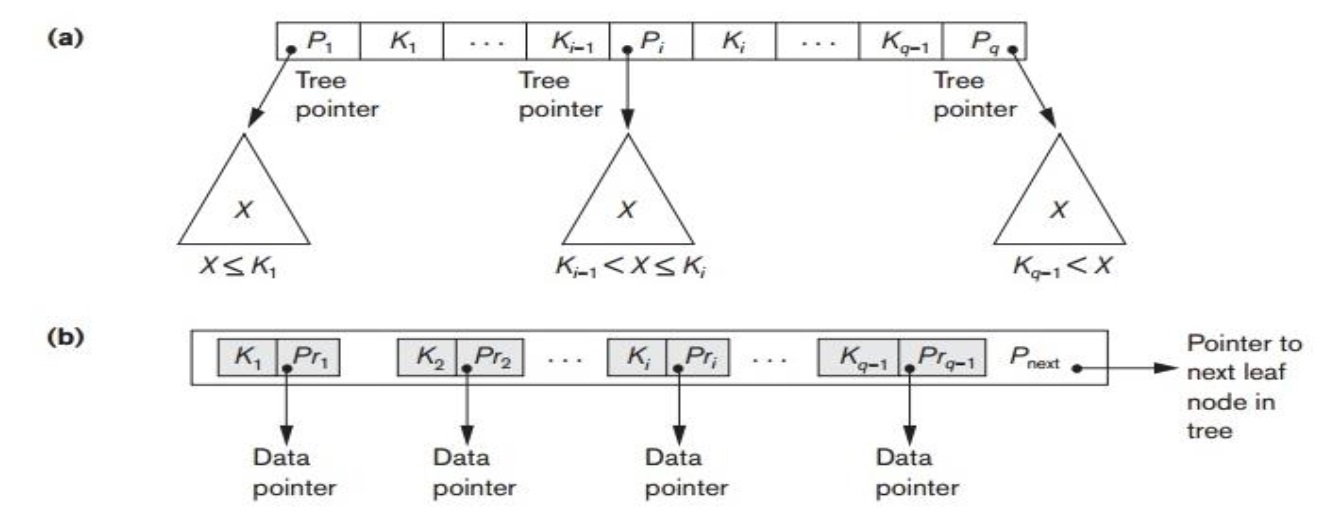
The document indexing process aims to store documents in a manner that facilitates the process of retrieving specific documents efficiently in terms of accuracy and time complexity. Many information retrieval systems encounter security issues and execution time to retrieve relevant documents. In addition, these systems lead to ample storage. Therefore, it requires combining confidentiality with the indexed document, and a separate process is performed to encrypt the documents. Hence, a new indexing structure named tree browser (TB) was proposed in this paper to be applied to index files of the large document set in an encrypted manner. This method represents the keywords in a variable-length binary format before being stored in the index. This binary format provides additional encryption to the information stored and reduces the index size. The proposed method (TB) is applied to the WebKB dataset. This dataset is related to web page documents (semi-structured documents). The experimental results demonstrated that the storage size is reduced by using TB-tree to 48.5 MB, while the traditional index is 307 MB.
Downloads
References
H. W. Oleiwi, N. Saeed, and H. S. Al-Raweshidy, “A Cooperative SWIPT-Hybrid-NOMA Pairing Scheme considering SIC imperfection for THz Communications,” Proc - 2022 IEEE 4th Glob Power, Energy Commun Conf GPECOM 2022, no. June, pp. 638–643, 2022, doi: 10.1109/GPECOM55404.2022.9815677.
H. W. Oleiwi and H. Al-Raweshidy, “SWIPT-Pairing Mechanism for Channel-Aware Cooperative H-NOMA in 6G Terahertz Communications,” Sensors, vol. 22, no. 16, p. 6200, 2022, doi: 10.3390/s22166200.
H. W. Oleiwi and H. Al-Raweshidy, “Cooperative SWIPT THz-NOMA/6G Performance Analysis,” Electron, vol. 11, no. 6, 2022, doi: 10.3390/electronics11060873.
H. W. Oleiwi, D. N. Mhawi, and H. Al-Raweshidy, “MLTs-ADCNs: Machine Learning Techniques for Anomaly Detection in Communication Networks,” IEEE Access, vol. 10, no. August, pp. 1–1, 2022, doi: 10.1109/access.2022.3201869.
H. W. Oleiwi, N. Saeed, and H. Al-Raweshidy, “Cooperative SWIPT MIMO-NOMA for Reliable THz 6G Communications,” Network, vol. 2, no. 2, pp. 257–269, 2022, doi: 10.3390/network2020017.
R. Reinanda, E. Meij, and M. De Rijke, “Knowledge graphs: An information retrieval perspective,” Foundations and Trends in Information Retrieval, vol. 14, no. 4. pp. 1–159, 2020, doi: 10.1561/1500000063.
S. Ceri, A. Bozzon, M. Brambilla, E. Della Valle, P. Fraternali, and S. Quarteroni, “An Introduction to Information Retrieval,” in Web Information Retrieval, 2013, pp. 3–11.
Z. Wang, K. Banawan, and S. Ulukus, “Private Set Intersection: A Multi-Message Symmetric Private Information Retrieval Perspective,” in IEEE Transactions on Information Theory, 2022, vol. 68, no. 3, doi: 10.1109/TIT.2021.3125006.
A. Karim Abdul Hassan and D. Enteesha mhawi, “A Proposed Method for Documents Indexing,” Diyala J Pure Sci, vol. 13, no. 2, pp. 43–56, 2017, doi: 10.24237/djps.1302.144a.
A. K. Hassan and D. Enteesha mhawi, “Enhance Inverted Index Using in Information Retrieval,” vol. 34, no. 2, 2016.
N. Wang, J. Fu, B. K. Bhargava, and J. Zeng, “Efficient Retrieval Over Documents Encrypted by Attributes in Cloud Computing,” IEEE Trans Inf Forensics Secur, vol. 13, no. 10, pp. 2653–2667, 2018, doi: 10.1109/TIFS.2018.2825952.
A. K. Doaa Nteesha Mhawi, “Information Retrieval Using Modified Genetic Algorithm,” Al mansour J, no. June, p. 15, 2017, doi: 10.36541/0231-000-027-004.
N. Al-ufoq and N. A. Company, The 3rd International Scientific Conference of Computer Sciences ( 3SCCS2021 ), no. January. 2022.
D. N. Mhawi and A. Aldallal, “Advanced Feature-Selection-Based Hybrid Ensemble Learning Algorithms for Network Intrusion Detection Systems,” Symmetry (Basel), vol. 14, no. 7, p. 1461, 2022.
H. Oleiwi, N. Saeed, H. Al-Taie, and D. Mhawi, “An Enhanced Interface Selectivity Technique to Improve the QoS for the Multi-homed Node,” Eng Technol J, vol. 40, no. 8, pp. 101–109, 2022, doi: 10.30684/etj.2022.133066.1165.
H. Oleiwi, N. Saeed, H. Al-Taie, and doaa nteesha “Evaluation of Differentiated Services Policies in Multihomed Networks Based on an Interface-Selection Mechanism,” Sustainability 2022, vol. 14, pages13235. https://doi.org/10.3390/su142013235.
G. E. Blelloch, J. T. Fineman, P. B. Gibbons, Y. Gu, and J. Shun, “Sorting with asymmetric read and write costs,” in Annual ACM Symposium on Parallelism in Algorithms and Architectures, 2015, vol. 2015-June, pp. 1–12, doi: 10.1145/2755573.2755604.
G. Ramachandran and K. Selvakumar, “Dynamic caching for semantic oriented adaptive search in unstructured P2P networks,” Asian J Inf Technol, vol. 13, no. 3, pp. 138–149, 2014.
R. J. Derscheid, M. C. Rahe, E. R. Burrough, K. J. Schwartz, and B. Arruda, “Disease diagnostic coding to facilitate evidence-based medicine: current and future perspectives,” J Vet Diagnostic Investig, vol. 33, no. 3, pp. 419–427, 2021, doi: 10.1177/1040638721999373.
R. Jin, H. J. Cho, S. W. Lee, and T. S. Chung, “Lazy-split B+-tree: A novel B+-tree index scheme for flash-based database systems,” in Design Automation for Embedded Systems, 2013, vol. 17, no. 1, pp. 167–191, doi: 10.1007/s10617-013-9123-4.
L. Yang, M. Di, X. Huang, and F. Duan, “BlockB-Tree: A new index structure combined compact B+-tree with block distance,” in Proceedings - 2015 8th International Congress on Image and Signal Processing, CISP 2015, 2016, pp. 533–538, doi: 10.1109/CISP.2015.7407937.
Y. Chen et al., “An Optimizing and Differentially Private Clustering Algorithm for Mixed Data in SDN-Based Smart Grid,” IEEE Access, vol. 6, 2018.
F. Boucenna, O. Nouali, S. Kechid, and M. Tahar Kechadi, “Secure Inverted Index Based Search over Encrypted Cloud Data with User Access Rights Management,” J Comput Sci Technol, vol. 34, no. 1, pp. 133–154, 2019, doi: 10.1007/s11390-019-1903-2.
D. A. Bonilla, A. Pérez-Idárraga, A. Odriozola-Martínez, and R. B. Kreider, “The 4r’s framework of nutritional strategies for post-exercise recovery: A review with emphasis on new generation of carbohydrates,” International Journal of Environmental Research and Public Health, vol. 18, no. 1. pp. 1–19, 2021, doi: 10.3390/ijerph18010103.
M. Fekihal, I. Jaluta, and D. K. Saini, “TB±tree: Index structure for Information Retrieval Systems,” 2015 2nd Int Conf Comput Sci Comput Eng Soc Media, CSCESM 2015, no. September, pp. 182–186, 2015, doi: 10.1109/CSCESM.2015.7331890.
D. N. Mhawi and S. H. Hashem, “Proposed Hybrid Correlation Feature Selection Forest Panalized Attribute Approach to advance IDSs,” Karbala Int J Mod Sci, vol. 7, no. 4, pp. 405–420, 2021, doi: 10.33640/2405-609X.3166.
M. S. Kadhm, “An Accurate Diabetes Prediction System Based on K-means Clustering and Proposed Classification Approach,” Int J Appl Eng Res, vol. 13, no. 6, pp. 4038–4041, 2018, [Online]. Available: https://www.ripublication.com/ijaer18/ijaerv13n6_118.pdf.
M. S. Kadhm, D. E. Mhawi, and R. M. H. Zaki, “An Accurate Handwritten Digits Recognition system Based on DWT and FCT,” Iraqi J Sci, vol. 58, no. 4B, pp. 2200–2210, 2017, doi: 10.24996/ijs.2017.58.4b.23.
H. W. Oleiwi, H. L. Al-Taie, N. Saeed, and D. N. Mhawi, “A Comparative Investigation on Different QoS Mechanisms in Multi-Homed Networks,” Iraqi J Ind Res, vol. 9, no. 1, pp. 1–11, 2022, doi: 10.53523/ijoirvol9i1id141.
V. Goel, A. K. Ahalawat, and M. N. Gupta, “Distributed air indexing scheme for full-text search on multiple wireless channel,” in Advances in Intelligent Systems and Computing, 2016, vol. 385, pp. 125–135, doi: 10.1007/978-3-319-23258-4_12.
A. Al-Dallal, “Enhancing recall and precision in Web search using advanced fitness function,” in Proceedings of the European, Mediterranean, and Middle Eastern Conference on Information Systems, EMCIS 2012, 2012, pp. 29–41.
D. N. Mhawi, Oleiwi, H.W., Saeed, N.H., Al-Taie, H.L. “An Efficient Information Retrieval System Using Evolutionary Algorithms,”. Network 2022, vol. 2, pp. 583-605., doi.org/10.3390/network2040034.
Downloads
Published
How to Cite
Issue
Section
License
Copyright (c) 2023 Doaa N. Mhawi, Haider W. Oleiwi, Heba L. Al-Taie

This work is licensed under a Creative Commons Attribution 4.0 International License.
















