Medical Image Encryption and Decryption Based on DNA: A Survey
DOI:
https://doi.org/10.51173/jt.v5i3.1134Keywords:
DNA Cryptography, Digital Medical Image, Encryption, DecryptionAbstract
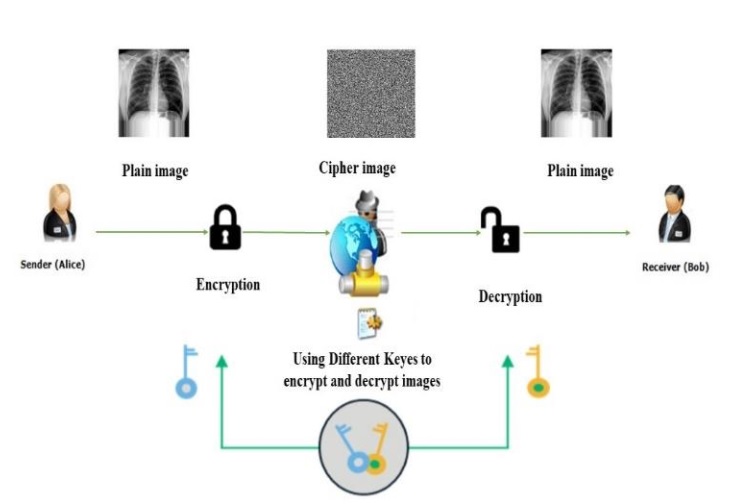
In the medical field, advanced techniques such as e-health, intelligent health, and telemedicine apps are being deployed. These approaches use open-source networks to send digital medical images. Patients’ private and sensitive diagnosis is contained in the digital medical image. Then sent the digital medical images are used for diagnosis by the remote center. For this reason, protecting patient privacy and the integrity of medical images is of paramount importance. DNA Digital coding is the most popular form of cryptographic technology, and it is frequently employed to strengthen information security, and the most prevalent constraints of DNA cryptographic schemes feature a high degree of temporal and algor. If DNA is employed appropriately, it can be used to achieve a number of security technologies, including encryption, steganography, signature, and authentication through the use of DNA molecules as information carriers. In this paper, a survey on the digital medical image was done. This survey contains the methods of encryption, and decryption of the image which is based on DNA with all the related methods and makes the comparison between the previous papers and explain which is the best to use.
Downloads
References
M. A. Iliyasu, O. A. Abisoye, S. A. Bashir, and J. A. Ojeniyi, “A review of DNA cryptograhic approaches,” Proc. 2020 IEEE 2nd Int. Conf. Cyberspace, CYBER Niger. 2020, pp. 66–72, 2021, doi: 10.1109/CYBERNIGERIA51635.2021.9428855.
M. A. Naji et al., “Breaking A Playfair Cipher Using Single and Multipoints Crossover Based on Heuristic Algorithms,” 4th Int. Iraqi Conf. Eng. Technol. Their Appl. IICETA 2021, pp. 47–53, 2021, doi: 10.1109/IICETA51758.2021.9717757.
N. S. Noor, D. A. Hammood, A. Al-Naji, and J. Chahl, “A Fast Text-to-Image Encryption-Decryption Algorithm for Secure Network Communication,” Computers, vol. 11, no. 3, 2022, doi: 10.3390/computers11030039.
S. Padhiar and K. H. Mori, “A Comparative Study on Symmetric and Asymmetric Key Encryption Techniques,” 2022, pp. 132–144. doi: 10.4018/978-1-7998-6988-7.ch008.
C. Tominski, G. Fuchs, and H. Schumann, “Task-driven color coding,” Proc. Int. Conf. Inf. Vis., pp. 373–380, 2008, doi: 10.1109/IV.2008.24.
N. S. Noor, D. A. Hammood, and A. Al-naji, “Applying TTIED-CMYK Algorithm in Wireless Sensor Networks Based on,” vol. 4, no. 3, pp. 1–7, 2022.
L. Wang, T. Dong, and M. F. Ge, “Finite-time synchronization of memristor chaotic systems and its application in image encryption,” Appl. Math. Comput., vol. 347, pp. 293–305, 2019, doi: 10.1016/j.amc.2018.11.017.
R. S. Jebur, C. S. Der, and D. A. Hammood, “A Review and Taxonomy of Image Denoising Techniques,” 6th Int. Conf. Interact. Digit. Media, ICIDM 2020, no. Icidm, 2020, doi: 10.1109/ICIDM51048.2020.9339674.
G. Ye, C. Pan, X. Huang, and Q. Mei, “An efficient pixel-level chaotic image encryption algorithm,” Nonlinear Dyn., vol. 94, no. 1, pp. 745–756, 2018, doi: 10.1007/s11071-018-4391-y.
C. TİKEN and R. SAMLI, “A Comprehensive Review About Image Encryption Methods,” Harran Üniversitesi Mühendislik Derg., vol. 8733, pp. 27–49, 2022, doi: 10.46578/humder.1066545.
H. Kaur and A. Kakkar, “Comparison of different image formats using LSB Steganography,” 4th IEEE Int. Conf. Signal Process. Comput. Control. ISPCC 2017, vol. 2017-Janua, pp. 97–101, 2017, doi: 10.1109/ISPCC.2017.8269657.
K. K. S. Pareek, Narendra K, Vinod Patidar, “A Symmetric Encryption Scheme for Colour BMP Images,” IJCA Spec. Issue “Network Secur. Cryptogr., no. January, pp. 42–46, 2011.
F. Alshehri and G. Muhammad, “A Comprehensive Survey of the Internet of Things (IoT) and AI-Based Smart Healthcare,” IEEE Access, vol. 9, pp. 3660–3678, 2021, doi: 10.1109/ACCESS.2020.3047960.
G. Muhammad, M. F. Alhamid, and X. Long, “Computing and processing on the edge: Smart pathology detection for connected healthcare,” IEEE Netw., vol. 33, no. 6, pp. 44–49, 2019, doi: 10.1109/MNET.001.1900045.
J. A. Kaw, N. A. Loan, S. A. Parah, K. Muhammad, J. A. Sheikh, and G. M. Bhat, “A reversible and secure patient information hiding system for IoT driven e-health,” Int. J. Inf. Manage., vol. 45, no. March, pp. 262–275, 2019, doi: 10.1016/j.ijinfomgt.2018.09.008.
G. Muhammad, M. S. Hossain, and N. Kumar, “EEG-Based Pathology Detection for Home Health Monitoring,” IEEE J. Sel. Areas Commun., vol. 39, no. 2, pp. 603–610, 2021, doi: 10.1109/JSAC.2020.3020654.
P. Sarosh, S. A. Parah, and G. M. Bhat, “An efficient image encryption scheme for healthcare applications,” Multimed. Tools Appl., vol. 81, no. 5, pp. 7253–7270, 2022, doi: 10.1007/s11042-021-11812-0.
M. Kaur, S. Singh, and M. Kaur, “Computational Image Encryption Techniques: A Comprehensive Review,” Math. Probl. Eng., vol. 2021, no. i, 2021, doi: 10.1155/2021/5012496.
Y. Xie, J. Yu, S. Guo, Q. Ding, and E. Wang, “Image encryption scheme with compressed sensing based on new three-dimensional chaotic system,” Entropy, vol. 21, no. 9, 2019, doi: 10.3390/e21090819.
M. Kaur and V. Kumar, “A Comprehensive Review on Image Encryption Techniques,” Arch. Comput. Methods Eng., vol. 27, no. 1, pp. 15–43, 2020, doi: 10.1007/s11831-018-9298-8.
M. A. Alhija, N. Turab, A. Abuthawabeh, H. Abuowida, and J. Al Nabulsi, “Dna Cryptographic Approaches: State of Art, Opportunities, and Cutting Edge Perspectives,” J. Theor. Appl. Inf. Technol., vol. 100, no. 18, pp. 5346–5358, 2022.
R. Enayatifar, A. H. Abdullah, and I. F. Isnin, “Chaos-based image encryption using a hybrid genetic algorithm and a DNA sequence,” Opt. Lasers Eng., vol. 56, pp. 83–93, 2014, doi: 10.1016/j.optlaseng.2013.12.003.
X. Wei, L. Guo, Q. Zhang, J. Zhang, and S. Lian, “A novel color image encryption algorithm based on DNA sequence operation and hyper-chaotic system,” J. Syst. Softw., vol. 85, no. 2, pp. 290–299, 2012, doi: 10.1016/j.jss.2011.08.017.
O. H. Alhabeeb, F. Fauzi, and R. Sulaiman, “A Review of Modern DNA-based Steganography Approaches,” Int. J. Adv. Comput. Sci. Appl., vol. 12, no. 10, pp. 184–196, 2021, doi: 10.14569/IJACSA.2021.0121021.
G. Cui, C. Li, H. Li, and X. Li, “DNA computing and its application to information security field,” 5th Int. Conf. Nat. Comput. ICNC 2009, vol. 6, no. February, pp. 148–152, 2009, doi: 10.1109/ICNC.2009.27.
A. Gehani, T. Labean, and J. Reif, “LNCS 2950 - DNA-based Cryptography,” pp. 167–188, 2004.
“DNA Structure. Base Pairing and Nucleotide Stock Vector - Illustration of genome, medicine: 239446702.” https://www.dreamstime.com/dna-structure-base-pairing-nucleotide-cytosine-thymine-guanine-adenine-vector-illustration-image239446702 (accessed Oct. 29, 2022).
C. R. Geyer, T. R. Battersby, and S. A. Benner, “Nucleobase Pairing in Expanded Watson-Crick-like Genetic Information Systems,” Structure, vol. 11, no. 12, pp. 1485–1498, 2003, doi: 10.1016/j.str.2003.11.008.
A. Nath, “International Journal of Advance Research in Introduction to Malware and Malware Analysis : A brief overview,” no. November, 2016.
S. Jain and V. Bhatnagar, “Analogy of various DNA based security algorithms using cryptography and steganography,” Proc. 2014 Int. Conf. Issues Challenges Intell. Comput. Tech. ICICT 2014, pp. 285–291, 2014, doi: 10.1109/ICICICT.2014.6781294.
K. Gupta and S. Singh, “DNA Based Cryptographic Techniques: A Review,” Int. J. Adv. Res. Comput. Sci. Softw. Eng., vol. 3, no. 3, p. 2277, 2013, doi: 10.6633/IJNS.201811.
B. B. Raj and V. Ceronmani Sharmila, “An survey on DNA based cryptography,” 2018 Int. Conf. Emerg. Trends Innov. Eng. Technol. Res. ICETIETR 2018, pp. 1–3, 2018, doi: 10.1109/ICETIETR.2018.8529075.
C. K. Volos, I. M. Kyprianidis, and I. N. Stouboulos, “Image encryption process based on chaotic synchronization phenomena,” Signal Processing, vol. 93, no. 5, pp. 1328–1340, 2013, doi: 10.1016/j.sigpro.2012.11.008.
Q. Zhang and J. Han, “A novel color image encryption algorithm based on image hashing , 6D hyperchaotic and DNA coding,” pp. 13841–13864, 2021.
H. A. M. A. Basha, A. S. S. Mohra, T. O. M. Diab, and W. I. El Sobky, “Efficient Image Encryption Based on New Substitution Box Using DNA Coding and Bent Function,” IEEE Access, vol. 10, no. May, pp. 66409–66429, 2022, doi: 10.1109/ACCESS.2022.3183990.
J. Yu, W. Xie, Z. Zhong, and H. Wang, “Image encryption algorithm based on hyperchaotic system and a new DNA sequence operation,” Chaos, Solitons and Fractals, vol. 162, no. July, p. 112456, 2022, doi: 10.1016/j.chaos.2022.112456.
C. Zou, X. Wang, C. Zhou, S. Xu, and C. Huang, “A novel image encryption algorithm based on DNA strand exchange and diffusion,” Appl. Math. Comput., vol. 430, 2022, doi: 10.1016/j.amc.2022.127291.
S. A. Elsaid, E. R. Alotaibi, and S. Alsaleh, “A robust hybrid cryptosystem based on DNA and Hyperchaotic for images encryption,” Multimed. Tools Appl., 2022, doi: 10.1007/s11042-022-12641-5.
S. Suri and R. Vijay, “A synchronous intertwining logistic map-DNA approach for color image encryption,” J. Ambient Intell. Humaniz. Comput., vol. 10, no. 6, pp. 2277–2290, 2019, doi: 10.1007/s12652-018-0825-0.
A. ur Rehman and X. Liao, “A novel robust dual diffusion/confusion encryption technique for color image based on Chaos, DNA and SHA-2,” Multimed. Tools Appl., vol. 78, no. 2, pp. 2105–2133, 2019, doi: 10.1007/s11042-018-6346-1.
“2021A medical image cryptosystem using bit‑level difusion with DNA.pdf.”
R. Ismail, A. Fattah, H. M. Saqr, and M. E. Nasr, “An efficient medical image encryption scheme for (WBAN) based on adaptive DNA and modern multi chaotic map,” Multimed. Tools Appl., 2022, doi: 10.1007/s11042-022-13343-8.
X. Xue, H. Jin, D. Zhou, and C. Zhou, “Medical Image Protection Algorithm Based on Deoxyribonucleic Acid Chain of Dynamic Length,” Front. Genet., vol. 12, no. March, pp. 1–18, 2021, doi: 10.3389/fgene.2021.654663.
R. Guesmi and M. A. B. Farah, “A new efficient medical image cipher based on hybrid chaotic map and DNA code,” Multimed. Tools Appl., vol. 80, no. 2, pp. 1925–1944, 2021, doi: 10.1007/s11042-020-09672-1.
P. Pavithran, S. Mathew, S. Namasudra, and P. Lorenz, “A novel cryptosystem based on DNA cryptography and randomly generated mealy machine,” Comput. Secur., vol. 104, p. 102160, 2021, doi: 10.1016/j.cose.2020.102160.
V. R. F. Signing, R. L. T. Mogue, J. Kengne, M. Kountchou, and Saïdou, “Dynamic phenomena of a financial hyperchaotic system and DNA sequences for image encryption,” Multimed. Tools Appl., vol. 80, no. 21–23, pp. 32689–32723, 2021, doi: 10.1007/s11042-021-11180-9.
W. Ran, E. Wang, and Z. Tong, “A double scrambling-DNA row and column closed loop image encryption algorithm based on chaotic system,” PLoS One, vol. 17, no. 7 July, pp. 1–30, 2022, doi: 10.1371/journal.pone.0267094.
D. Wei and M. Jiang, “A fast image encryption algorithm based on parallel compressive sensing and DNA sequence,” Optik (Stuttg)., vol. 238, no. February, p. 166748, 2021, doi: 10.1016/j.ijleo.2021.166748.
D. Ravichandran, A. Banu S, B. K. Murthy, V. Balasubramanian, S. Fathima, and R. Amirtharajan, “An efficient medical image encryption using hybrid DNA computing and chaos in transform domain,” Med. Biol. Eng. Comput., vol. 59, no. 3, pp. 589–605, 2021, doi: 10.1007/s11517-021-02328-8.
X. Zhang and Y. Hu, “Multiple-image encryption algorithm based on the 3D scrambling model and dynamic DNA coding,” Opt. Laser Technol., vol. 141, no. January, p. 107073, 2021, doi: 10.1016/j.optlastec.2021.107073.
Downloads
Published
How to Cite
Issue
Section
License
Copyright (c) 2023 Saja Theab Ahmed, Dalal Abdulmohsin Hammood, Raad Farhood Chisab, Nurulisma Binti Hj. Ismail

This work is licensed under a Creative Commons Attribution 4.0 International License.
















